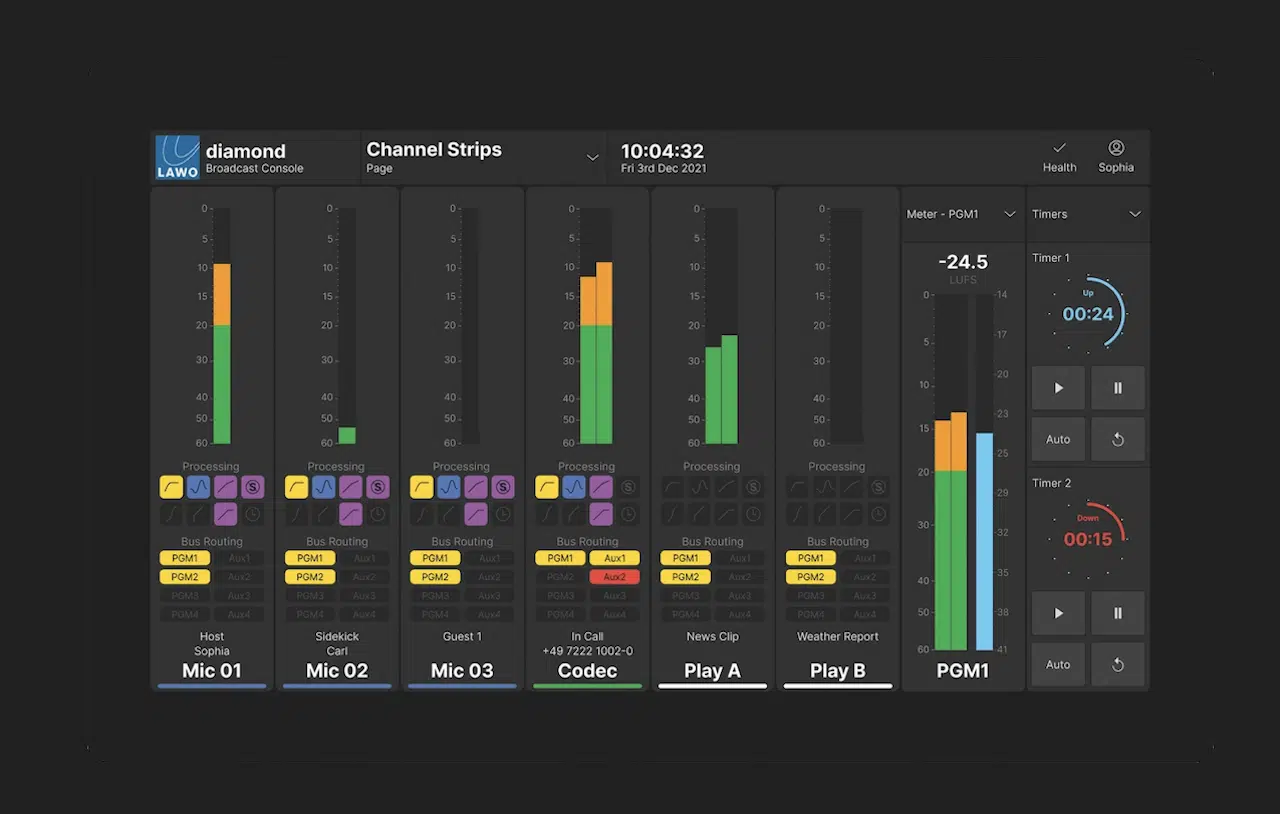
It’s an unfortunate fact that radio stations make excellent targets for hackers — a hit is almost guaranteed to make the news and generate significant exposure.
It’s also probably true that every radio station thinks it has taken the necessary precautions to protect itself. But no radio station is bulletproof when it comes to cybersecurity — it is only as strong as its weakest link. Such links are not necessarily digital in nature; they can be a curious staff member clicking on a seemingly innocuous or otherwise encouraging link in an email. A notification from Amazon of a delivery they didn’t order? A click on the info link is all that is needed to start a process that can silence a radio station.
This is the modus operandi of hackers employing the Cryptolocker virus. Once a staff member clicks on the link and inadvertently downloads the virus, it is in the system. It then has an incubation period during which it examines the network, looking for media files and further points of vulnerability.
The Risks
Once it discovers media files — such as audio files — it puts a “wrapper” around them, essentially cutting off the system’s access to the audio. It then generates a pop-up notification informing users that the files are locked. A security key will unlock the files — for a fee, paid in Bitcoin.
During this time, the on-air studio scheduling system reports that the audio file for every scheduled song and commercial cannot be found. The backup system — if connected to the network — is also infected.
No radio station is bulletproof when it comes to cybersecurity — it is only as strong as its weakest link.
The pop-up notification also comes with a countdown. Unless the station pays the listed amount by the end of the countdown, the ransom amount increases. For most stations at that point, the only option is to suck it up and pay up.
Most cyberattacks utilize weaknesses in the Windows operating system, so any onsite system that runs on Windows — including a radio station’s scheduling system — is particularly susceptible. Hence the logic behind a cloud strategy for running a radio station’s on-air operations.
However, not all “cloud-based solutions” are solutions to the problem. There are “false-cloud” claims. Companies claim that they “run software in the cloud” but are simply using Windows-based servers in countries where such services are cheap. “Proper” cloud servers use “container” systems running on Linux.
Protecting Your Operations

According to Philippe Generali, president and CEO of RCS Worldwide, cybersecurity is one of the most significant benefits of a cloud-based programming strategy. If a radio station’s entire on-air system is continually backed up in the cloud, it is checked for integrity, ready at a moment’s notice should there be any disruption. Hacking is not the only threat to a radio station’s operations — a careless staff member can easily delete audio files.
There are other benefits to a cloud-based strategy. One of those is that there is no upfront CapEx — no large servers requiring storage space and equipment rooms to house them. No equipment is needed to maintain. Furthermore, there is no software or hardware to update and no need for licensing fees. A cloud strategy runs on a “pay-as-you-go” usage platform.
In addition, any authorized person can access a cloud-based system from any internet-linked device. A station’s technician doesn’t have to plug into the station’s system manually. They can log in using a laptop or tablet from anywhere.
One of the biggest advantages of a cloud-based strategy is the opportunity for collaboration and the flexibility it provides. Multiple people with qualified authority can collaborate on the same station, the same log, and without running into conflict, because all the changes happen in the same shared location. A radio station’s team — be they involved in scheduling or presenting — can be based anywhere.
It is probably the last point that really drew attention to the benefits of cloud-based programming strategies over the past few years as the COVID-19 pandemic pressured radio stations to keep staff at home whenever they could. But like the virus, hackers never rest — they’re continually looking for the weakest link and an opportunity to benefit from it. There’s probably never been a better time to consider a cloud-based strategy.